Launching a Deep Scan
In this article, we will go over you can easily start a deep scan on a single or multiple URLs or even a target definition to uncover vulnerabilities.
What are Deep Scans?
Contrary to a Recon Scan, Deep Scan is a scan that is executed once in a workflow-like method to uncover as many web security vulnerabilities on your target URLs or assets.
Starting a Deep Scan on a single URL
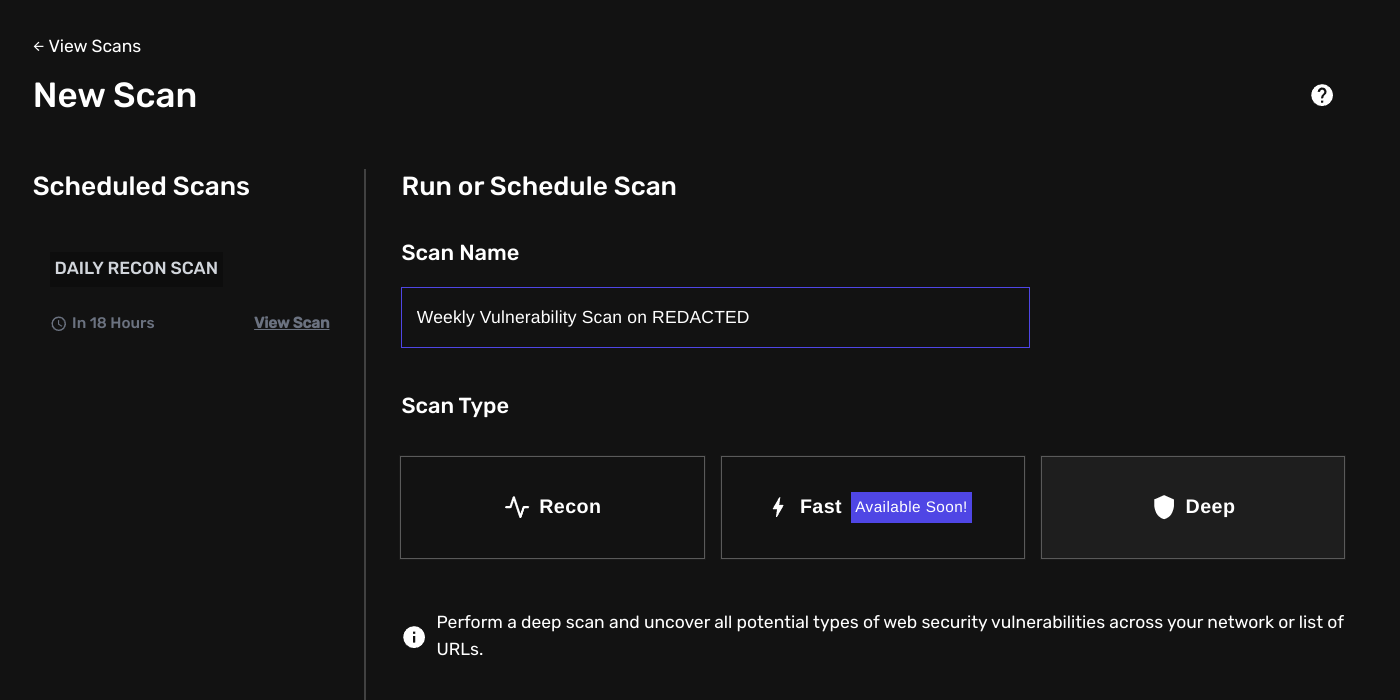
To start or launch a Deep Scan:
- Navigate to
/scans/new - Select Deep Scan
- And under the Target section, specify a single URL, a list of URLs or a select a predefined asset definition from the list.

If your Target Definition does not have any URLs attached, it will automatically first perform a reconnaissance scan to map out all possible in-scope live hosts.
Please make sure you provide valid URLs. Not providing any valid URLs may result in some of the scans to fail.
Next, in case you want to schedule your scan or configure it to run on a recurring basis, enable the option “Schedule Scan”.
What this will do is unfold the options menu for you to specify a future date to which you would like to run the scan. You can also configure it to only run once.

The default timezone is set to GMT, you may change it on your profile settings
Afterward, you may also configure what security vulnerabilities you would like to scan for. By default, all are selected. And it is also possible to provide request headers to be sent with each single request (authenticated scanning is possible).
Lastly, you may also want to specify a time delay (between each request sent) to comply with any scope or assessment rules or just to make sure to not overload the target.

And finally, click on Run Scan to run the scan. You will be redirected in a moment to the results page.
Live Results: The scanner is capable of saving the first results as soon as they are available. This may mean that your scan is marked as “finished” but still has a few scans running in the background.
You can consult the Scans tab in your Deep Scan result page to view the status of each individual child process launched.
What happens after I start a Deep Scan?
The workflow is optimized to uncover as much many vulnerabilities as possible. The scanner first starts off with a thourough content discovery scan. This scan (performed by SPIDER X) is responsible for gathering all possible links, paths, app routes, API endpoints, files, and (query) parameters through various methods like:
- Headless crawling (including intercepting requests, listening for various browser events and enumerating links)
- JavaScript Code Analysis
- HTTP Response Analysis
- Public Web Archives
- Common Config Files (like
robots.txtandsitemap.xml) - And soon also targeted bruteforcing with dynamically generated wordlists based on a few key parameters (like technologies, language, common naming patterns, etc.)
After the content discovery scan finishes, it will automatically pass the data to the next scanners to scan for for example CWE-89 (SQL Injections) or CWE-77 (Command Injections).
WAYPOINTS Integration
WAYPOINTS is our new template-based scanner which allows you to define scanner rules and find all sorts of security vulnerabilities. This can significantly help increase the discovery of 0-day and 1-day security vulnerabilities (often used to gain initial foothold into an organisation’s network).
By default, all private templates created and tagged with “DEEPSCAN” will be ran by default on the selected URL(s). Learn more about WAYPOINTS and Creating a Template.
